![]()
![]()
![]()
![]() The Murderous Clinton Crime Empire: A Devastating Expose
The Murderous Clinton Crime Empire: A Devastating Expose
http://www.jar2.com/Topics/Clinton_Crimes.html
![]()
![]()
![]() WikiLeaks
US Election Meddling Goes Back to 2012
WikiLeaks
US Election Meddling Goes Back to 2012
http://www.jar2.com/Wikileaks/2012/October/US_Elections.html
![]()
![]()
![]() The Arrest of Paul Hawkins
The Arrest of Paul Hawkins
![]()
![]()
![]() WikiLeaks
Main Page
WikiLeaks
Main Page
http://www.jar2.com/Topics/WikiLeaks.html
![]()
![]()
![]() The
Killings of WikiLeaks: MI6 Tied to Seth Rich, Gareth Williams and Other
WikiLeaks' Kills: UK Ambassador-MI6 Asset/Officer Craig Murray Met Seth
Rich. There Was No Hacker
The
Killings of WikiLeaks: MI6 Tied to Seth Rich, Gareth Williams and Other
WikiLeaks' Kills: UK Ambassador-MI6 Asset/Officer Craig Murray Met Seth
Rich. There Was No Hacker
http://www.jar2.com/Wikileaks/The_Killings_of_WikiLeaks.html
http://www.jar2.com/Files/Downloads/The-Killings-of-WikiLeaks-002.mp3
![]()
![]()
![]() These Are the Actual Original Untouched Leaks That Exposed the Fake
Democracy
These Are the Actual Original Untouched Leaks That Exposed the Fake
Democracy
http://www.jar2.biz/Files/DNC.zip
http://www.jar2.biz/Files/DCCC/Trove%205/web/doudj0pm.html
![]()
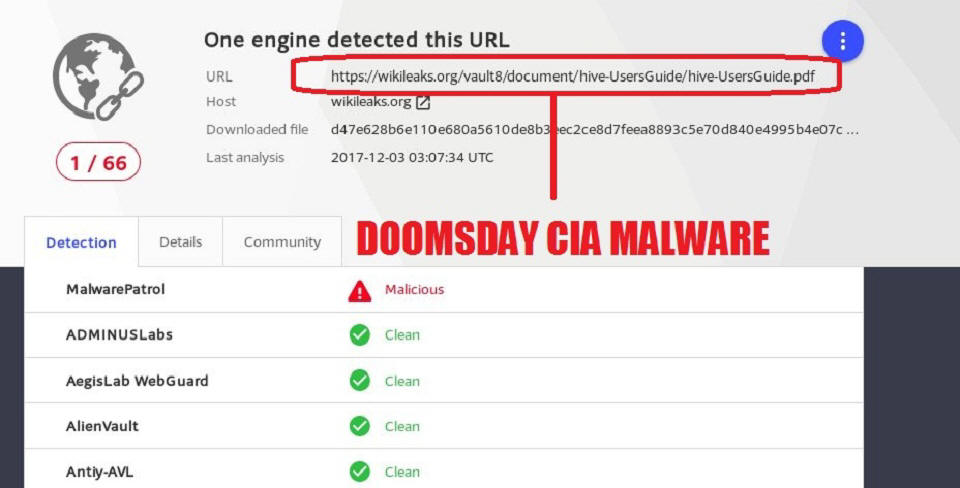
The CIA/WikiLeaks Doomsday Virus - Military Grade Malware
![]()

![]()
![]() CIA/WL Malware Infection and the Doomsday Software You Downloaded - December
2017
CIA/WL Malware Infection and the Doomsday Software You Downloaded - December
2017
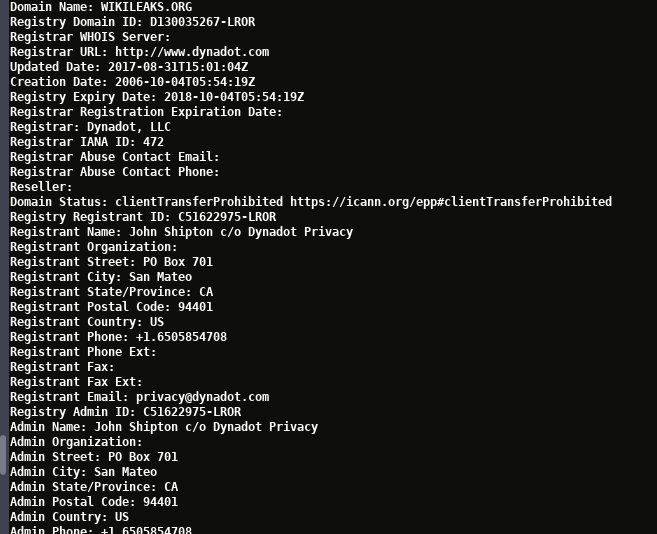
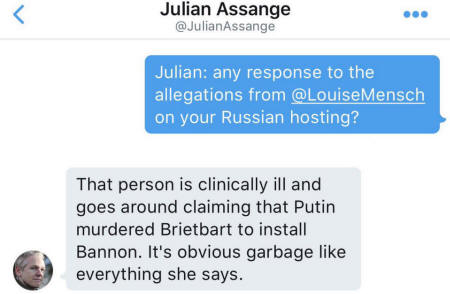
On the second of December the now CIA controlled
WikiLeaks changed their DNS information to portray two of their IP addresses
as being in the Russian Federation. Since we know that WikiLeaks is one
hundred percent CIA controlled any change to DNS or Domain Registrar
information is cause for investigation so me and the alert member of
Anonymous who gave me the heads up started investigating.
Changing DNS information is nothing sinister in and
of itself, if ISPs are changed, or physical location is moved or servers are
added or subtracted are just some of the normal reasons one might change
their IP and DNS. However, in this case there is something much more
sinister going on, even worse than just lying to the world and pretending to
be an organization that was taken over and no longer exists in order to get
away with evil.
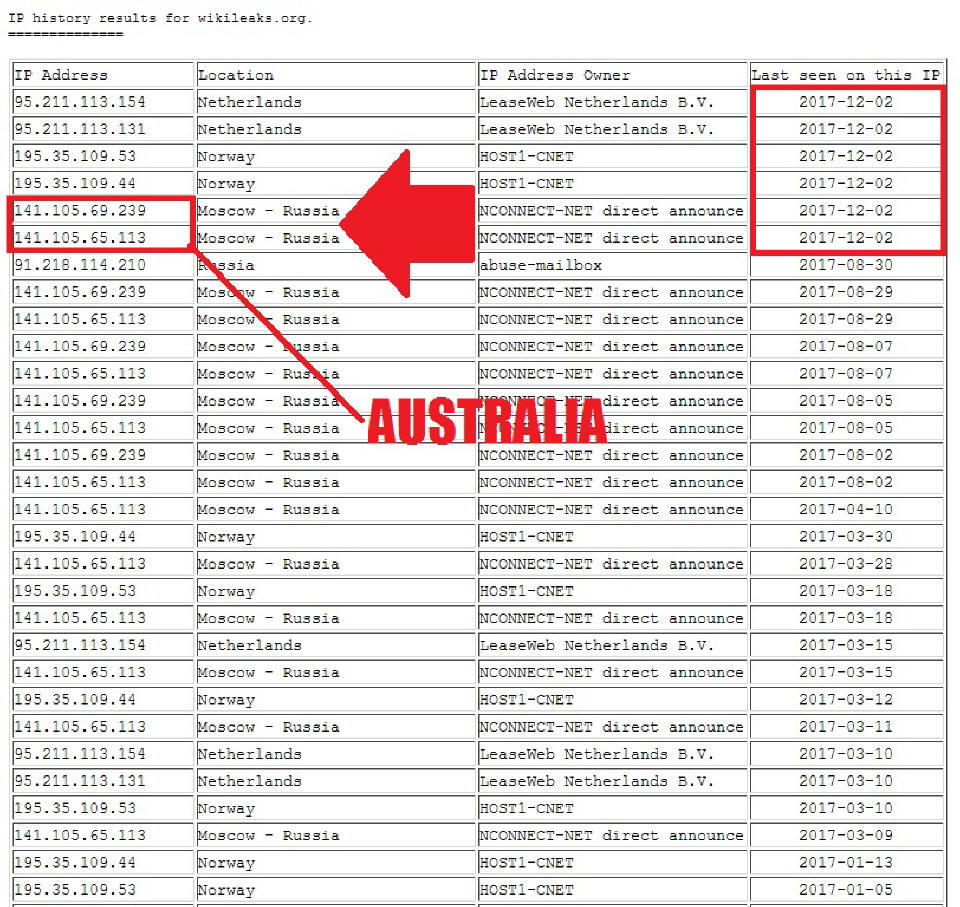
Above I said portray because the IP addresses
141.105.65.11. and 141.105.69.239 which are listed as owned by NCONNECT-NET,
with locations in Moscow Russia, are actually physically located in
Australia. Again nothing sinister in and of itself but when tied in with
more, and there is much more, things start to look pretty dark.
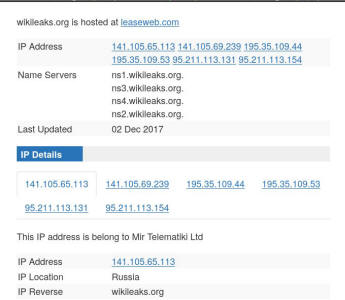
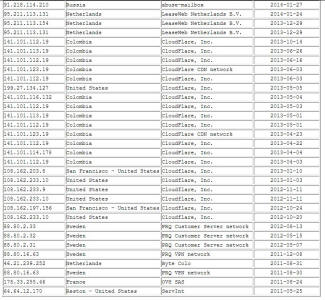 WL's First IP??? Reston Virginia
WL's First IP??? Reston Virginia
Another change was the addition of a company called
Mir Telematiki Ltd as the Russian owner of IP address 141.105.65.113 which
also Traceroutes to Australia, but appears to place WikiLeaks servers in
Moscow. The other Norwegian and Dutch addresses are pretty much unchanged
and actually refer to the real locations so I am not mentioning them at all.
So someone controlling WikiLeaks at the CIA is
trying to give WikiLeaks a Russian connection, this is obvious, but why?
Here is where the story really starts to get scary.
Several Anonymous people and myself started
investigating further and an old laboratory White Hat from way back when, a
hacker’s hacker if you will, and someone we all admire (we meaning those who
know of this person) made a frightening discovery about one of the files on
WikiLeaks. Actually there were several but his was the worst and is still
being investigated and which I will get into in a minute.
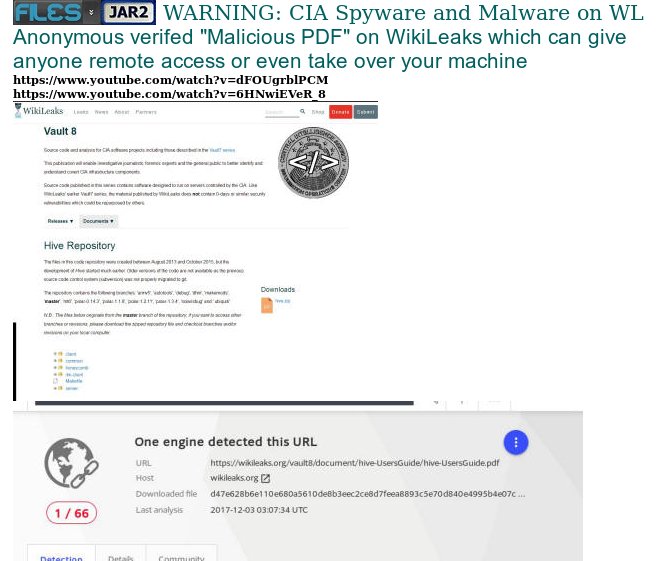
One of the LULSEC 2.0s or Anonymous people
immediately became alarmed when they noticed that WL is using off-site
storage and in this case a hive, which is something they have never done
before and which we are also investigating as it is not what it appears to
be. One of the big discoveries was related to this hive and various code
hidden in the innocuous looking PDF file which is supposed to be
instructions for working with the hive, but again this is not too sinister
until you put all the pieces together.
The next piece of the puzzle involves the Vault 7/8
releases. I am a journalist and fairly tech savvy so some of this stuff
might be of interest to me but since, as a former WikiLeaks associate , I am
100% certain WL is completely under CIA control, I stay as far away from WL
and the Vault BS as possible. However one must ask themselves why WL is
presenting these programs and using a hive and telling people to verify
version numbers and such in the directories on their comps etc., when this
is supposed to be about journalism and exposing the CIA. Normal journalist
do not have the coding skills or the forensic computer programs and
equipment, let alone the knowledge, to take these programs apart and see
what they really do, so like I have been saying for over a year, it is all a
bunch of tick –tock bullshit. Or is it?
The penultimate piece of the
technical puzzle is the hive repository and the files with such names as
honeycomb and ilm client. Hives, honeycomb, bees, tick-tock, tick-tock
(Honey Trap Boom?)… The files in the repository basically allow the CIA to
access everything you have or do on your computer, wi-fi and all your
connected devices and gather them into the proper directories which you may
not even see and which may be hidden on, for example, the Windows install
partition, which normally no one worries or even knows about.
I have perhaps said to much already because I do
not want them to know how good or bad we are nor what we know so in the
classic cat and mouse of hacking and computer security I will not go into
too much detail and will cut to the chase.
The final piece of this tick-tock is a file
infected with a new virus, new malware, that is something that our White
Hats have never seen before. One of the things it does is install security
certificates on your comps or devices giving it whatever privileges it
desires and installs certificates to get around every anti-virus or
anti-malware program except Kaspersky Labs, meaning Kaspersky would be the
only program to see this threat, a fact from which we can ascertain that
this is why they have been kicked out of the US Government sector.
The malware in question does many things and I am
not at liberty to say all of them yet! With the Vault files and the other
pieces in place, the attack is so complex and involved that an entire team
is still trying to figure it out and will probably only have an answer in a
few days. Here is what I can say: the file we have looked at is a “Back Door
Bot” that no one has seen anything like before. It installs hidden Magnetic
Links, meaning the upload processes to CIA or wherever, uses the Torrent
system (which explains why we still have it) and other P2P protocols and can
re-write itself re-name itself and targets almost all mobile and PC systems.
It is new and thus has no name yet but I have suggested calling it Kolya,
after the nazi apologist kid (a long story). Our only advice right now is do
not download or even open anything from WL even a text file and delete
anything you downloaded from WikiLeaks since October 16th, 2016 when it was
taken over.
Now the BOOM part; this is my own conclusion and I
would hope I am wrong but unfortunately I have not been so far. As we do not
know what exactly we are dealing with it is early to give a definitive
answer as to what it will do exactly but my scenario is as follows: given
the propaganda that the US government has pushed that WL and hackers and
hacking are the same as terrorism or military attacks the entire package
looks like a platform which will give the CIA the fictitious massive
cyberattack from Russia that they dream about and will use to start their
long planned World War III. The package explains the ridiculous insistence
on debunked claims of Russian interference in US elections and the like,
which I know for a fact are lies because we know exactly who delivered the
Clinton, Podesta and DNC files.
If the CIA has created a Doomsday cyber-attack
weapon and can create a Russian attack scenario by infecting half the
world’s computers with malware and then one day triggers it, causing untold
havoc worldwide, will the world be that upset if the US uses its
self-declared “right” to a pre-emptive nuclear strike on Russia?
Knowing what I know the scenario is not only
possible but frighteningly likely.
>>>>>>>
Please spread this far and wide. If the world knows
in advance we may be able to stop the lunatics who are working night and day
to ensure their New World Order and our destruction.
Stay tuned and stay awake.
We have been warning you for years about something
like this! ALL TICK TOCKING ends in BOOM. They have been warning us
X
![]()
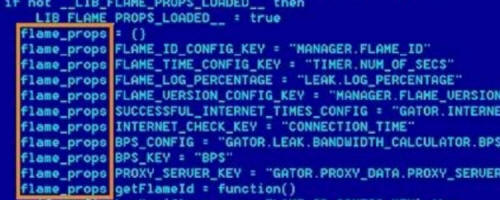
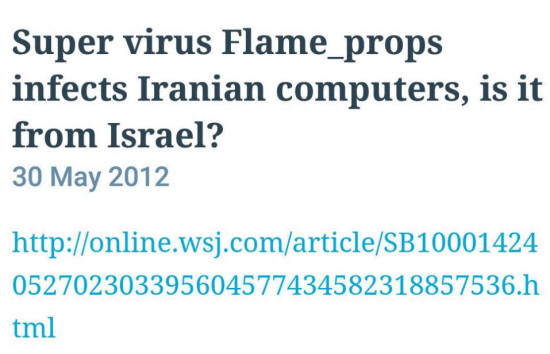
![]() Update One: Part of the Doomsday Package on WL Contains the Flame_props Super
Virus
Update One: Part of the Doomsday Package on WL Contains the Flame_props Super
Virus
![]()
![]() Update Two After Analysis: Conclusion - CIA, Name: The Doomsday Virus
Update Two After Analysis: Conclusion - CIA, Name: The Doomsday Virus
First Look: Magnet links with no metadata. Never seen anything like this before
Very strange looks local .. US
Never seen magnet link intrusion though multiple OSes
The links were done in ascii/ binary I thinks it's a reuse of old code but using a p2p
May be a test of a takeover. Tried a p2p tracker in Flud Magnets only good for like 27 seconds, Pretty creepy....
Server action somewhere analyzing the injecting files.
There's a password 256 bit using renovo code extractor
Considering that x86 instructions have variable sizes, and that data and instructions can be interleaved in x86 executables, i associate each byte of the memory space with a flag. Since this flag has only two states: clean and dirty, it can be represented as 1 bit...etc...
Final Analysis Being Sent to Anti-Virus Companies Now
It is a Backdoor Bot
Uses P2P to download based on your OS version
Targets Android/IOS/Windows
Uses media extensions for IOS/Android
Uses Common win32hlp.cnf for Windows
Will flash ROM and Ghost Copy Hard Drives - Very complicated attack
Certificates match past certs
90% American, the sub routines match what is taught in America in structure, even the spacing of the code and the character structure. I was made on a Windows PC in English.
Takes background update for P2P
In pro registers a Domain
Domain name has retarded character length
In IOS the target is the i8.
There are 1.5 million lines of code in multiple formats (roughly)
PDF is the carrier
Bypasses extension check with self generated error which injects and corrupts existing files with a piggback
Uses default Admin on Android
Uses factory key reset on IOS
Completely rapes Windows 7-10
Our White Hat lost three devices and is now sending to AVG and Malwarebytes
My conclusion CIA
![]()




_small.png)